How Improper Regex Usage Can Open Your System to Vulnerabilities
Discover the security risks of regex misuse in code, from SQL Injection to IDOR and CORS, and learn tips to protect against these vulnerabilities. Ideal for developers and penetration testers focused on secure coding.
Hey everyone, hope you're all doing great!
As a peneteration tester or even a developer, it's crucial to be careful with regex, because if you’re not, writing the wrong patterns can lead to vulnerabilities.
In the world of web development and security, proper input validation is paramount. Among the many tools developers use for validation, regular expressions (regex) stand out for their power and versatility. However, if not implemented correctly, regex can become a double-edged sword, leading to significant security vulnerabilities. This post will explore how improper use of regex can result in vulnerabilities such as SQL Injection (SQLI), Insecure Direct Object References (IDOR), and Cross-Origin Resource Sharing (CORS) issues. By understanding these risks, you can better protect your applications and users.
In this post, I want to share a few security tips about improper use of regex and its impact on common vulnerabilities like SQL Injection, IDOR, and CORS.
These tips can help you understand how poor security configurations can lead to serious vulnerabilities
So lets begin...
CORS (Cross-Origin Resource Sharing):
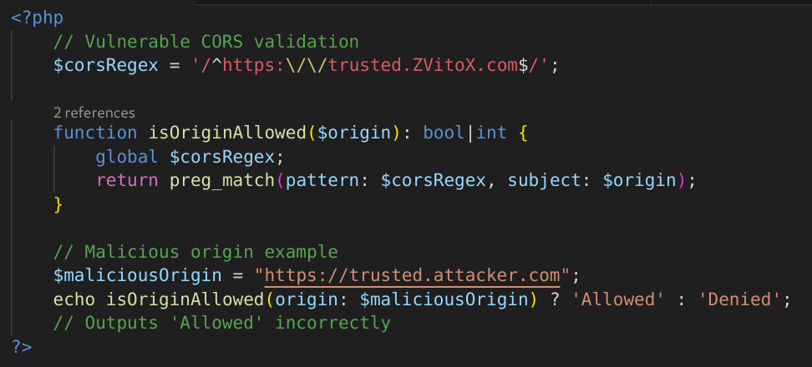
For example, a website might use the following regex to check the origin of requests:
But how can this regex lead to a CORS vulnerability?
Here, the developer forgot to escape the dot (.) with a backslash (\). As a result, any domain that starts with https://trusted would be allowed
This means an attacker could send requests from malicious domains like https://trusted.attacker.com and gain access to users data
As you know this vulnerability could lead to a serious data leak
💡 Quick Tip: Always use strict validation when setting up CORS policies to prevent accidental data exposure.
IDOR (Insecure Direct Object References):
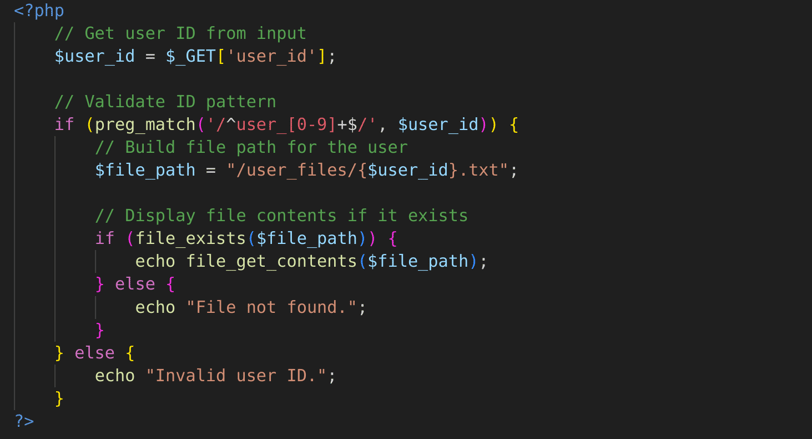
For instance, in a file management system, if a developer uses the following regex to validate IDs:
This regex validates only the ID pattern and fails to restrict access to other users' files.
An attacker could change user_1234 to user_5678 to access another user’s files.
This type of vulnerability could allow unauthorized file access or data manipulation.
💡 Quick Tip: Ensure access control measures go beyond pattern matching for sensitive data identifiers.
SQL Injection (Email Validation):
If an email validation regex like this is used:
The issue with this regex is that it can easily process special emails like fake@example.com' OR '1'='1 without proper validation
Ultimately, an attacker could bypass restrictions by inputting specific emails, potentially compromising the database
This problem could lead to unauthorized access
💡 Quick Tip: Always use parameterized queries to prevent SQL injection, even if inputs seem secure.
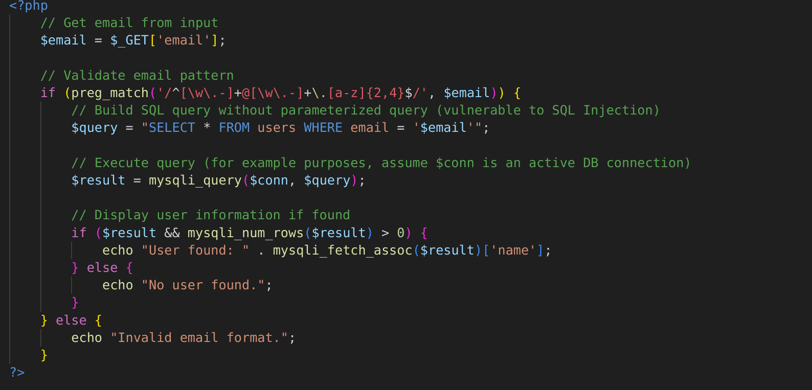
These examples highlight how improper use of regex can lead to severe vulnerabilities on websites.
I hope these insights help you to be more cautious with validation, especially regex, and security configurations.
As always, don't forget the golden rule:
Stay strong, Take action, Keep evolving.. 👑🩸
